How OSINT Experts Use Twitter To Combat Cybercrime
How OSINT Experts Use Twitter To Combat Cybercrime. Discover more detailed and exciting information on our website. Click the link below to start your adventure: Visit Best Website. Don't miss out!
Table of Contents
How OSINT Experts Use Twitter to Combat Cybercrime
The digital world is a double-edged sword. While offering unprecedented connectivity, it also provides fertile ground for cybercriminals. But fighting back is a dedicated community of Open Source Intelligence (OSINT) experts, and one of their most powerful weapons? Twitter. This seemingly innocuous social media platform is a goldmine of information, and savvy OSINT investigators are using it to track down cybercriminals, expose scams, and prevent future attacks.
Twitter: An Unexpected Crime-Fighting Tool
For many, Twitter is a place for news, opinions, and memes. However, for OSINT analysts specializing in cybersecurity, it's a rich tapestry of data, often revealing crucial clues about cybercriminal activities. Unlike encrypted communication channels favored by many malicious actors, Twitter often offers a trail of breadcrumbs—publicly available information that, when pieced together, can paint a comprehensive picture of a cybercrime operation.
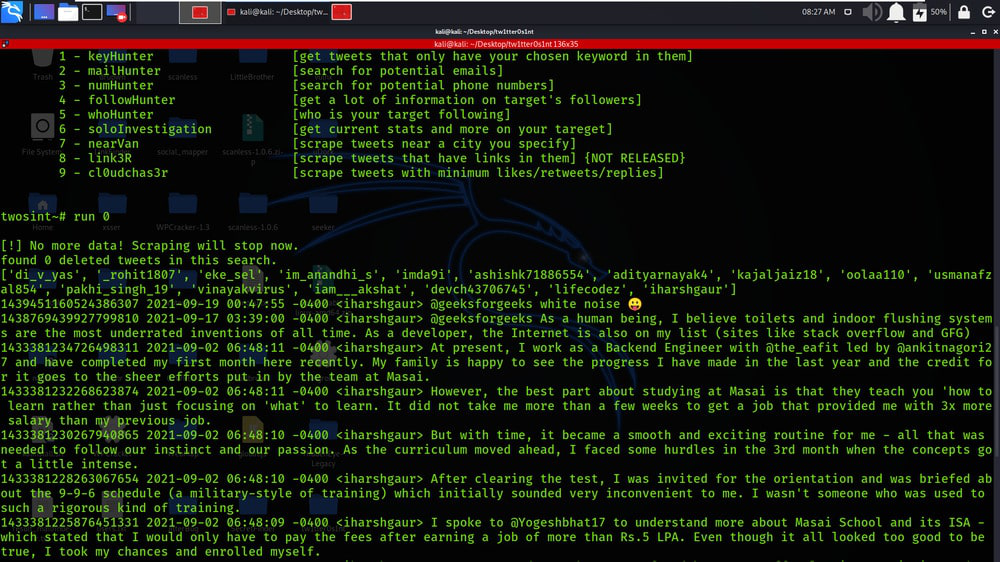
Techniques Employed by OSINT Experts on Twitter
OSINT experts use various techniques to leverage Twitter for cybersecurity investigations:
-
Keyword Searches: By monitoring specific keywords related to known malware, scams, or hacking groups, analysts can identify potential threats in real-time. This includes tracking hashtags associated with specific malware campaigns or searching for mentions of compromised accounts.
-
Account Analysis: Analyzing suspicious Twitter accounts can uncover vital information. Experts scrutinize profile details, tweets, retweets, followers, and following lists to identify links to criminal activity. Unusual posting patterns, affiliations with known malicious actors, and the use of specific language can all be strong indicators.
-
Hashtag Tracking: Hashtags are powerful tools. Tracking specific hashtags related to data breaches, ransomware attacks, or phishing scams allows experts to monitor the spread of malicious information and identify potential victims.
-
Geolocation Data: While not always precise, geolocation data from tweets can help investigators narrow down the location of cybercriminals, particularly those boasting about their activities.
-
Image and Video Analysis: Images and videos shared on Twitter can contain metadata revealing crucial information such as timestamps, location data, and device information, which can be used to corroborate other findings.
Case Studies: Real-World Examples
The use of Twitter in OSINT investigations has yielded significant results in numerous cases. For example, OSINT analysts have successfully:
-
Uncovered dark web marketplaces: By monitoring tweets containing specific keywords and links, investigators have identified and disrupted illegal online marketplaces dealing in stolen data and illicit services.
-
Tracked down ransomware operators: Analysis of tweets and associated accounts helped law enforcement agencies identify and apprehend individuals responsible for major ransomware attacks.
-
Exposed phishing scams: OSINT investigations using Twitter have exposed numerous phishing campaigns, preventing widespread damage and protecting countless potential victims.
The Importance of Ethical OSINT Practices
While Twitter is a powerful tool, ethical considerations are paramount. OSINT investigations must adhere to legal boundaries and respect privacy. Improper use of OSINT techniques can have serious legal ramifications. It's crucial for OSINT analysts to understand and comply with relevant laws and regulations.
Conclusion: The Future of OSINT and Twitter
The use of Twitter in OSINT investigations is constantly evolving. As cybercrime techniques become more sophisticated, so too will the methods used by OSINT experts to combat them. The integration of advanced analytical tools and machine learning will further enhance the capabilities of OSINT analysts using Twitter and other open-source platforms to fight cybercrime. The ongoing battle against cybercrime demands innovative approaches, and the role of OSINT experts utilizing platforms like Twitter is crucial in this fight for a safer digital world. Stay informed about the latest OSINT techniques and contribute to a safer online environment!

Thank you for visiting our website wich cover about How OSINT Experts Use Twitter To Combat Cybercrime. We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and dont miss to bookmark.
Featured Posts
-
 Investigating The Cause Two Rem Service Outages In One Day
Feb 05, 2025
Investigating The Cause Two Rem Service Outages In One Day
Feb 05, 2025 -
 Navigating Komodo Miami Reservations Dress Code And What To Expect
Feb 05, 2025
Navigating Komodo Miami Reservations Dress Code And What To Expect
Feb 05, 2025 -
 Flea Poop In Your Home Causes Prevention And Treatment
Feb 05, 2025
Flea Poop In Your Home Causes Prevention And Treatment
Feb 05, 2025 -
 Fantastic Four First Steps Poster Ai Generated
Feb 05, 2025
Fantastic Four First Steps Poster Ai Generated
Feb 05, 2025 -
 Exploring The Evolution Of Venom From Comic To Let There Be Carnage And Beyond
Feb 05, 2025
Exploring The Evolution Of Venom From Comic To Let There Be Carnage And Beyond
Feb 05, 2025
Latest Posts
-
 Used Cars In Fargo Craigslist Listings And Pricing
Feb 05, 2025
Used Cars In Fargo Craigslist Listings And Pricing
Feb 05, 2025 -
 Successions Shiv Roy Analyzing Her Moral Compass And Choices
Feb 05, 2025
Successions Shiv Roy Analyzing Her Moral Compass And Choices
Feb 05, 2025 -
 Understanding Turmeric And Dogs Health Benefits Risks And Safe Use
Feb 05, 2025
Understanding Turmeric And Dogs Health Benefits Risks And Safe Use
Feb 05, 2025 -
 What Time Is It In Boston Right Now A Quick Guide To Boston Time
Feb 05, 2025
What Time Is It In Boston Right Now A Quick Guide To Boston Time
Feb 05, 2025 -
 Court Appearance For Man Charged In Fentanyl Death Case
Feb 05, 2025
Court Appearance For Man Charged In Fentanyl Death Case
Feb 05, 2025
